Cybersecurity: What Is Insufficient Authentication?
Definition
Insufficient Authentication is a security vulnerability that refers to a situation in which important functions or resources can be accessed within an application or system without the proper authentication process.
List of Vulnerable Points
Pages that require authorization to access.
My Account (User Profile)
Discussion Boards or Forums
Methods to Verify Vulnerabilities
Verify if reauthentication is required when accessing the user profile.
Check if login is possible even with incorrect credentials.
Identify cases where authentication relies solely on the username.
Attack Methods
Attack Scenario
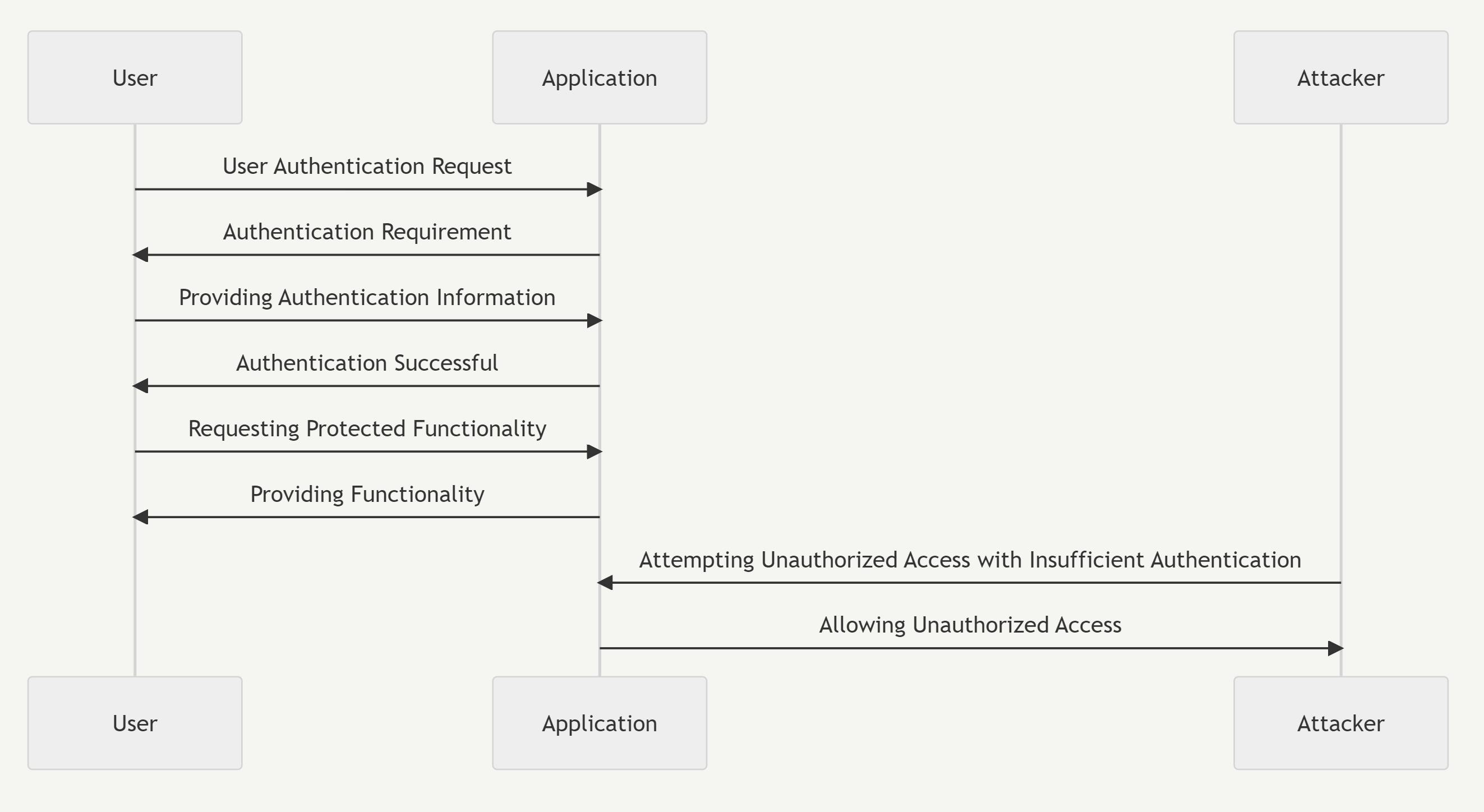
The attacker explores vulnerabilities that allow them to bypass or disable the authentication process.
They may bypass authentication using weak passwords or unauthorized access to a user's session.
Exploiting the vulnerabilities, the attacker gains unauthorized access to important functions or resources.
Process Flow
Mitigation Strategies
Implement and strengthen appropriate authentication procedures. Verify user identities and perform thorough authorization checks.
Establish secure password policies and enforce them. Use encryption for storing passwords and employ secure authentication mechanisms.
Carefully manage sessions and implement appropriate timeouts and logout functionality.
Enhance access controls for protected functions or resources to prevent unauthorized users from gaining access.