What is Session Prediction?
Definition
Session Prediction is a security vulnerability where an attacker predicts session identifiers to hijack or forge another user's session. Session identifiers are typically used in the form of cookies, tokens, or session IDs to maintain a user's authentication state and manage sessions.
Vulnerability Points of Occurrence
- All pages where sessions are applied.
Vulnerability Verification Methods
When there is a consistent algorithm for session issuance that makes prediction easy:
Verify if sessions are issued anew during login.
Check if sessions are related to different IDs.
Verify if sessions are related to time.
Ensure sessions do not remain unchanged.
Check encryption methods (e.g., MD5 not used, DES, SHA, etc.).
Attack Methods
Attack Scenario
Attackers use various techniques to predict session identifiers.
Attackers who have predicted session identifiers hijack or forge the user's session to bypass authentication.
Attackers use session identifiers to impersonate users, abusing the original user's privileges or performing illegal actions.
Occurrence Process
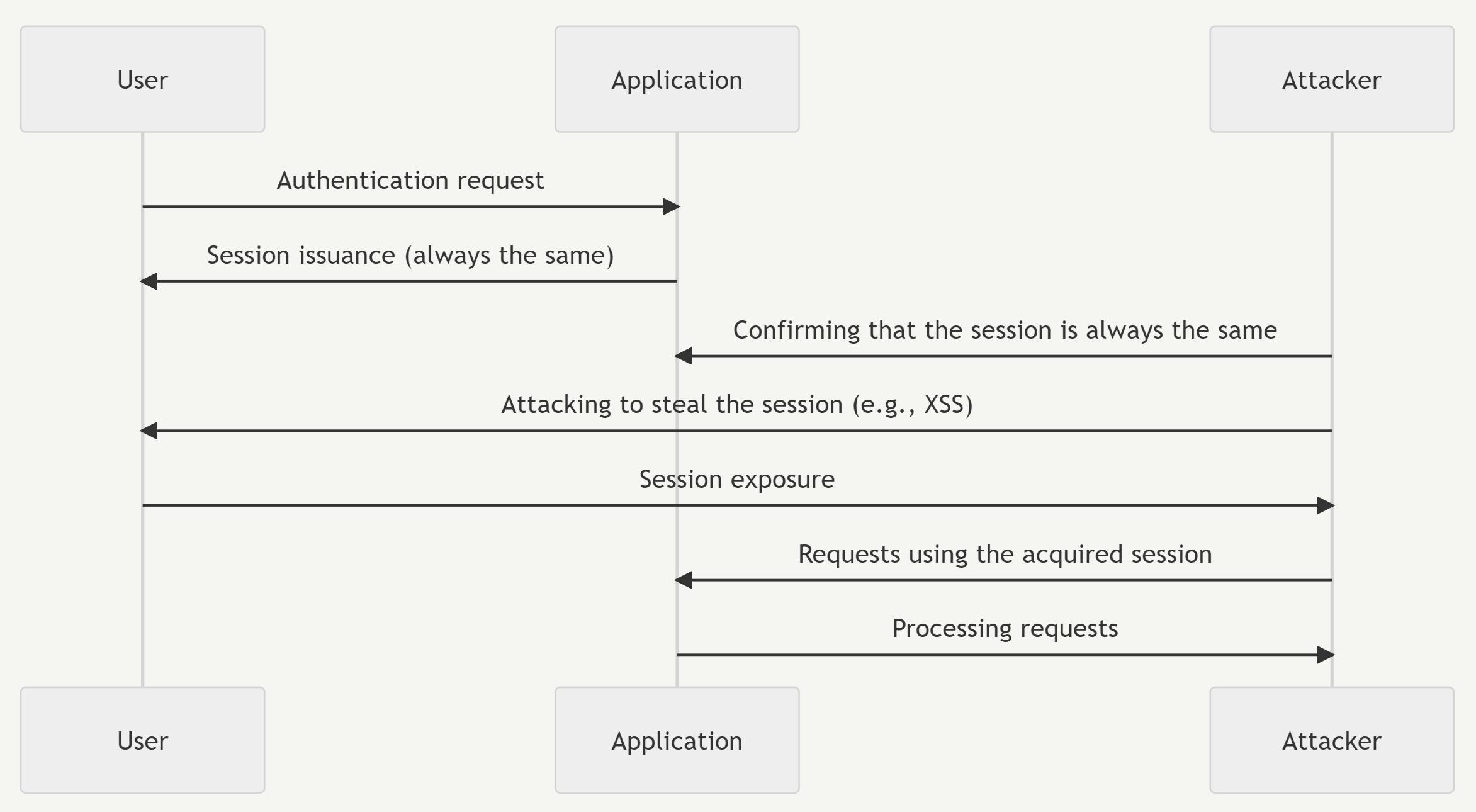
Detailed Process Explanation
The user requests authentication from the application.
The application issues a session to the user.
The attacker confirms that the session is the same as the user's ID.
The attacker uses various attack techniques (e.g., XSS) to obtain the session identifier.
The user exposes the session identifier to the attacker.
The attacker uses the acquired session identifier to send requests to the application.
The application processes the attacker's requests.
Mitigation Strategies
Use strong session identifier generation algorithms that are difficult to predict and have high randomness.
Strengthen session management and maintenance methods. Limit the validity period of sessions and renew them when necessary.
Implement secure session identifier transmission methods. Use encrypted connections like HTTPS or require additional authentication.